
If you're still running Windows 10 on your business machines, let's cut to the chase: The clock is ticking. On October 14, 2025, Microsoft is officially ending support for Windows 10. That means no more security...

You set it. You forget it. And just like that, while you're packing for vacation, your inbox starts automatically broadcasting: "Hi there! I'm out of the office until [date]. For urgent matters, please contact...

If you're only contacting your IT provider when it's time to renew your contract, you're missing the mark. Technology is not a "set it and forget it" aspect of your business. It's always changing, and so are the...

It's a quiet June morning. Half your team is on vacation. The other half is working from home or moving between coffee shops and hotel WiFi. Then it happens. Your system goes down. The printer stops working. No...

Your employees could be the largest cybersecurity threat to your business, not just because they might fall for phishing scams or reuse passwords, but because they are using applications that your IT department is...

If I asked you to identify the most significant cybersecurity threats in your office, you might mention phishing emails, malware, or weak passwords. However, what if I told you that your office printer—the one...
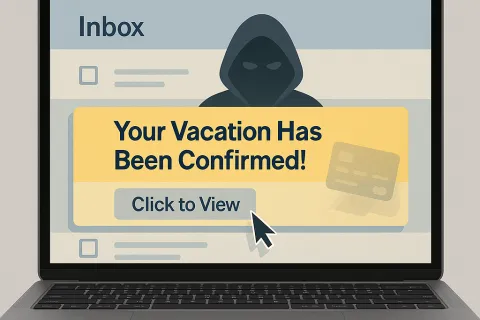
Planning a vacation this year? Ensure your confirmation email is legitimate BEFORE you click anything! Summer is approaching, and cybercriminals are taking advantage of the travel season by sending deceptive...

A client recently asked me about the most common mistakes business owners make regarding IT and cybersecurity. Where do I start? After years of working with various businesses, the most significant mistake I...

Chatbots such as ChatGPT, Gemini, Microsoft Copilot, and the newly launched DeepSeek have transformed our interactions with technology, assisting with a wide range of tasks from composing emails and creating content...